Secure Authentication-Management human-centric Scheme for trusting personal resource information on mobile cloud computing with blockchain
May 2018. By Young-Sik Jeong
Keyword: Human-centric authentication management, Mobile cloud computing, Blockchain, Resource management for human-centric
Recently, smartphones have rapidly become popular and research has been actively conducted on methods of making the character inputs that are most frequently used more convenient and faster. However, although many character input schemes have been developed, time is required for users to learn character input methods and typing errors frequently occur. In addition, many touches and movements are required for character inputs and the touch recognition elements of touch screens that are not high pressure types involve great inconvenience for disabled persons or patients who cannot use their fingers properly, as they cannot input the appropriate characters.
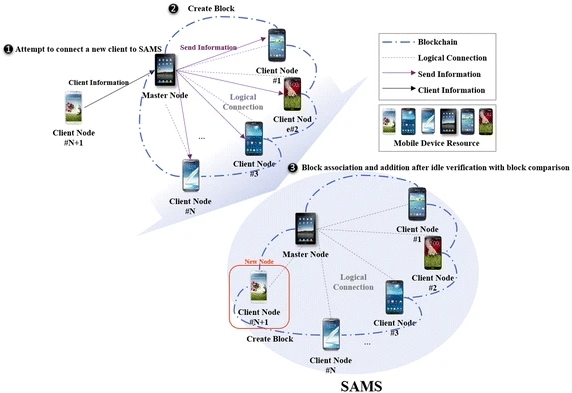
This research proposes the Secure Authentication Management human-centric Scheme (SAMS) to authenticate mobile devices using blockchain for trusting resource information in the mobile devices that are participating in the MRM resource pool. The SAMS forms a blockchain based on the resource information of the subordinate client nodes around the master node in the MRM. Devices in the MRM that have not been authorized through the SAMS cannot access or falsify data. To verify the SAMS for application with MRM, it was tested for data falsification by a malicious user accessing the SAMS, and the results show that data falsification is impossible.
